class: title, self-paced Finding CVE's with ease<br/> <!-- .nav[*Self-paced version*] --> .debug[ ``` ``` These slides have been built from commit: 00d7d7f [shared/title.md](https://git.verleun.org/training/containers.git/tree/main/slides/shared/title.md)] --- ## Introduction - Hello! I am: - 👴 Marco Verleun (marco.verleun@i-share.nl) - 🏢 Employed by i-share (www.i-share.nl) - 👷🏼♂️ Devops/GitOps/Cloud/Container/Cluster/Linux engineer (Pick one) - 🎯 Passion: Secure K8S clusters (air-gapped) running secure containers .debug[[sbom/intro.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/intro.md)] --- ## This presentation has a broad audience... We all have to make sure our host/network devices/containers/appliances are safe. This is a talk about software security, not the quality. And software is present in many places... And do try this at home! .debug[[sbom/intro.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/intro.md)] --- class: pic .interstitial[] --- name: toc-food-safety class: title Food safety .nav[ [Previous part](#toc-) | [Back to table of contents](#toc-part-1) | [Next part](#toc-why-use-sboms) ] .debug[(automatically generated title slide)] --- class: pic # Food safety ## Would you consume this? .center[] .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- class: pic ## Or this? .center[] .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- ## It probably depends... - A blank container is for the adventurous amongst us and might be delicious. - Other people might be more interested in nutritious facts. .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- ## It is nice to know what's inside It is nice to know what the contents of a product are before you decide if you want to consume it. Food labels are ment to do this without revealing a recipe. .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- class: pic ## Have a look at this .center[] .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- ## Why not do the same with our - Hardware - Software - Saas solutions - etc. .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- ## ...BOMs are there to help Have a look at <https://github.com/CycloneDX/bom-examples> We focus on SBOM during this talk. .debug[[sbom/food-safety.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/food-safety.md)] --- class: pic ## Remember this song? .center[] Whenever I talk about SBOMs René (a colleague) can't get this song out of his head. I hope you have the same experience and can't stop thinking about SBOMs... ??? Sex Bomb is a song from 1999 by Tom Jones and dj Mousse .debug[[sbom/tom-jones.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/tom-jones.md)] --- class: pic .interstitial[] --- name: toc-why-use-sboms class: title Why use SBOMs? .nav[ [Previous part](#toc-food-safety) | [Back to table of contents](#toc-part-2) | [Next part](#toc-examples) ] .debug[(automatically generated title slide)] --- # Why use SBOMs? .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- class: pic ## Do you want to deploy this? .center[] .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- ## And do you remember: * ShellShock * Log4J / Log4Shell * Heartbleed These also affected routers, printers and other devices at home. .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- class: pic ## Like food labels SBOMs tell you what's inside .center[] .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- ## Example SBOM snippet ```json { "id": "e1597ba21775e886", "name": "certifi", "version": "2022.12.7", "type": "python", "foundBy": "python-package-cataloger", "locations": [ { "path": "/usr/local/lib/python3.11/site-packages/certifi-2022.12.7.dist-info/METADATA", "layerID": "sha256:2ecbe4cb3d052a933e1cab8d573b14cfb4c50df323e4efde9cece026ce0fc73e", "annotations": { "evidence": "primary" ... "licenses": [ { "value": "MPL-2.0", "spdxExpression": "MPL-2.0", "type": "declared", ``` .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- class: pic ## More and more you can download them upfront .center[] .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- class: pic ## And analyze them before you install something .center[] .debug[[sbom/purpose-of-sbom.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/purpose-of-sbom.md)] --- class: pic .interstitial[] --- name: toc-examples class: title Examples .nav[ [Previous part](#toc-why-use-sboms) | [Back to table of contents](#toc-part-3) | [Next part](#toc-sbom-future) ] .debug[(automatically generated title slide)] --- # Examples ## Know what you deploy Imagine that you download and run a Python application in your cluster. Which one do you prefer and why given the following `Dockerfile`: ```Dockerfile FROM python:latest RUN pip install redis RUN pip install requests COPY worker.py / CMD ["python", "worker.py"] ``` ```Dockerfile FROM python:alpine RUN pip install redis RUN pip install requests COPY worker.py / CMD ["python", "worker.py"] ``` .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## The only difference is the base image But the end result is quite different: | Base image | Image size | CVE's | |---|---|---| | python:latest | 888 Mb | 1114 | | python:alpine | 73,5 Mb | 3 | (Scanning was done with `grype` and since the writing of this presentation the numbers have increased) .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## Using SBOMs to obtain foreknowledge of CVE's Knowing upfront which CVE's could be deployed is a check that can be done easily if the SBOM file is available. This can be a local file created inside a pipeline or an external file pulled during a build run. ```bash ❯ grype python.json ✔ Vulnerability DB [no update available] ✔ Scanned for vulnerabilities [1644 vulnerability matches] ├── by severity: 19 critical, 335 high, 473 medium, 74 low, 721 negligible (22 unknown) └── by status: 261 fixed, 1383 not-fixed, 0 ignored NAME INSTALLED FIXED-IN TYPE VULNERABILITY SEVERITY apt 2.2.4 deb CVE-2011-3374 Negligible bash 5.1-2+deb11u1 (won't fix) deb CVE-2022-3715 High binutils 2.35.2-2 deb CVE-2023-25588 Negligible ``` (This SBOM was created with the following command: `syft --output spdx-json python-latest:latest > python.json`) .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## Analyzing SBOMS in registries ```bash $ cosign verify-attestation --key /path/to/cosign.pub --type cyclonedx <IMAGE> > sbom.cdx.intoto.jsonl $ trivy sbom ./sbom.cdx.intoto.jsonl sbom.cdx.intoto.jsonl (alpine 3.7.3) ========================= Total: 2 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 2) ┌────────────┬────────────────┬──────────┬───────────────────┬───────────────┬──────────────────────────────────────────────────────────┐ │ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │ ├────────────┼────────────────┼──────────┼───────────────────┼───────────────┼──────────────────────────────────────────────────────────┤ │ musl │ CVE-2019-14697 │ CRITICAL │ 1.1.18-r3 │ 1.1.18-r4 │ musl libc through 1.1.23 has an x87 floating-point stack │ │ │ │ │ │ │ adjustment im ...... │ │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2019-14697 │ ├────────────┤ │ │ │ │ │ │ musl-utils │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └────────────┴────────────────┴──────────┴───────────────────┴───────────────┴──────────────────────────────────────────────────────────┘ ``` `cosign` is used to securely sign and verify software artifacts such as release files, container images, binaries, software bills of materials (SBOMs), and more. ??? Example taken from: https://aquasecurity.github.io/trivy/v0.33/docs/attestation/sbom/ .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## Deployment prevention in pipeline Inspecting SBOMs is best done before deploying containers and friends. Prevention is always best. The OCI standard allows storing SBOM information in container registries which could be nice for future use. The docker buildkit has builtin functionallity, eg: `docker buildx build --sbom=true -t <myorg>/<myimage> --push .` will automaticcaly create a SBOM and push it to the registry. SBOMs can be generated by other commands as well and stored in other places. Consider analyzing the information of the SBOM in a deployment pipeline and take action if necessary. .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## Storing SBOM information Often CVE's are discovered after deployment. Scanning a collection of SBOMs to see if the new CVE's affect the deployments is a relative cheap and quick process which can be done automaticcaly at regular intervals. Depending on the tools or application the SBOM info is stored in a container registry (e.g. docker buildx), filesystem (e.g. syft), configmap (e.g. kubeclarity) or a database (e.g. dependency track) .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- class: pic ## CVE's increase over time .center[] .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- ## Stored SBOM's Imagine that we store SBOM information in Dependency Track, or any other suitable application. Today a new zero day exploit is detected. How cool would it be to identify which host, devices, images etc. are affected without rescanning? The zero day is reported as `CVE-2023-49568` .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- class: pic ## Search for `CVE-2023-49568` .center[] .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- class: pic ## Obtain info about CVE .center[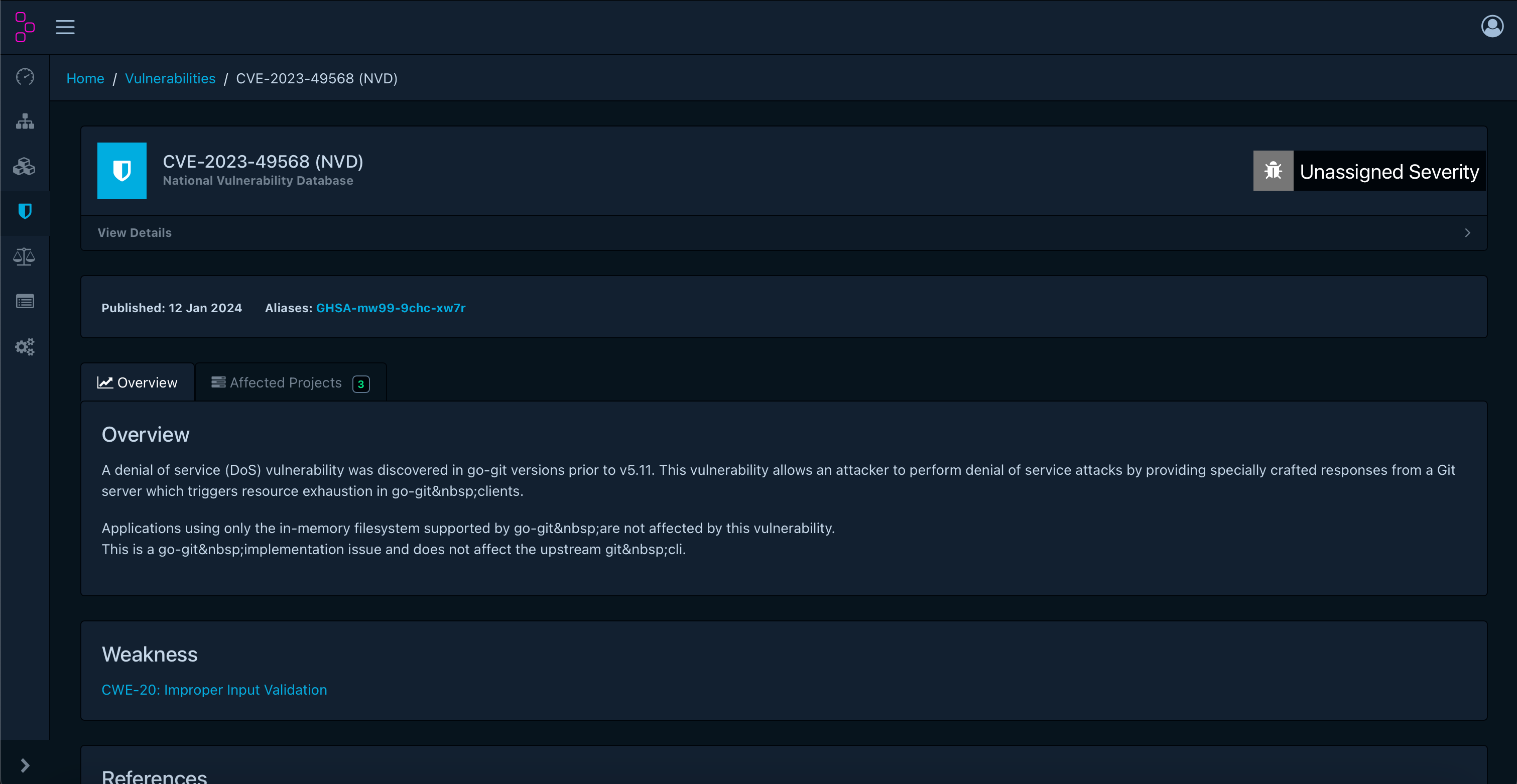] .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- class: pic ## Identify related projects .center[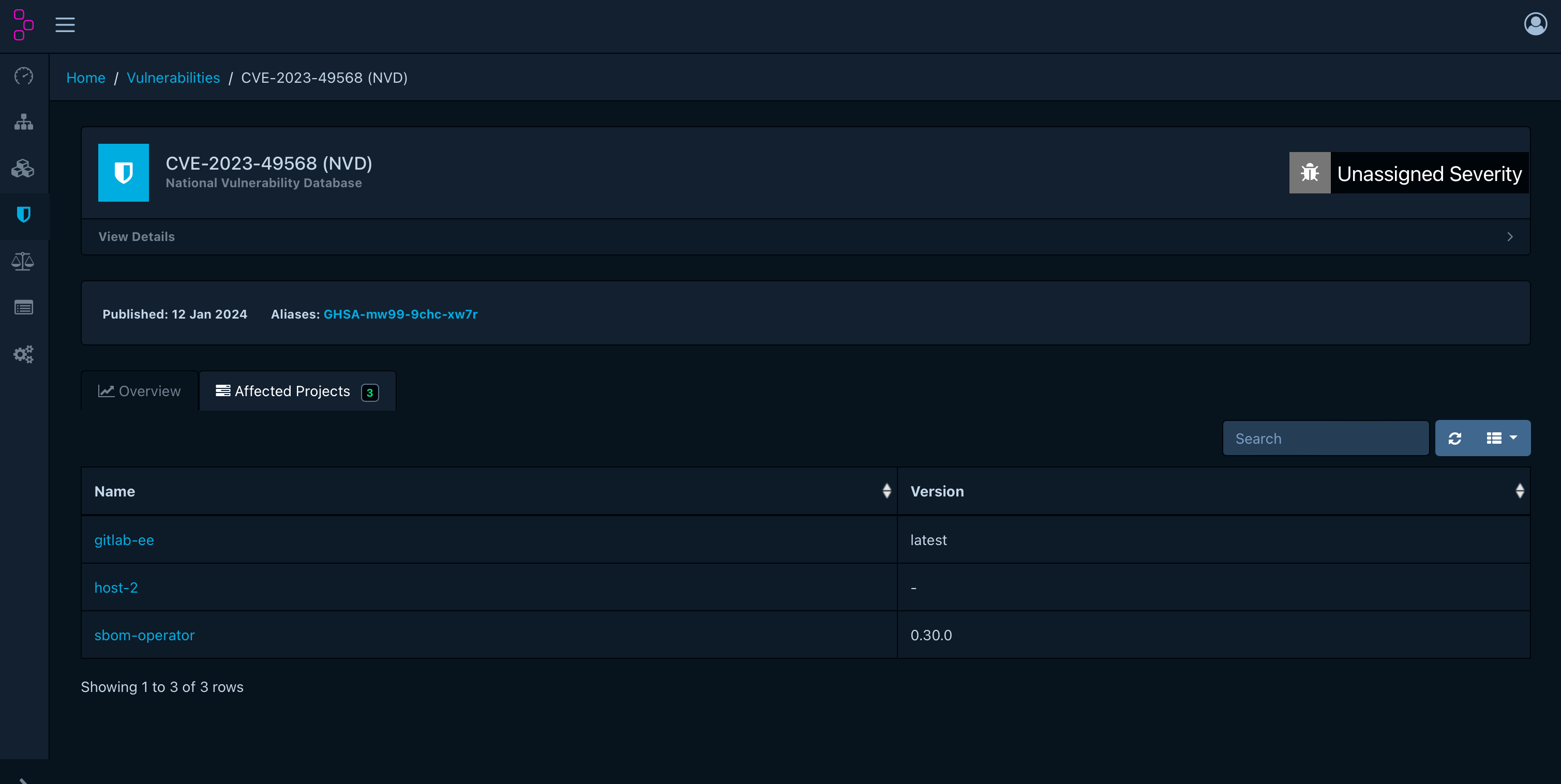] .debug[[sbom/sbom-examples.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/sbom-examples.md)] --- --- class: pic .interstitial[] --- name: toc-sbom-future class: title SBOM future .nav[ [Previous part](#toc-examples) | [Back to table of contents](#toc-part-4) | [Next part](#toc-interesting-links) ] .debug[(automatically generated title slide)] --- # SBOM future (This is entirely my personal opinion) ## Facts - The US Federal government requires SBOM's before purchasing a solution. - The dutch government strongly recommends SBOMs. - There is an increasing responsibility for vendors to provide (security) updates for a longer period. (e.g. smartphones, home routers etc.) - New critical CVE's will be discovered. .debug[[sbom/future.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/future.md)] --- ## Future - More companies scan their software during the build process. - More companies will request SBOM's before purchasing or using software. - Software companies will use SBOM's to be able to easily maintain their software. - And you will start to appreciate them too. .debug[[sbom/future.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/future.md)] --- ## Question - Which licenses are applicable? - Do they comply with business rules? .debug[[sbom/future.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/future.md)] --- class: pic .interstitial[] --- name: toc-interesting-links class: title Interesting links .nav[ [Previous part](#toc-sbom-future) | [Back to table of contents](#toc-part-5) | [Next part](#toc-) ] .debug[(automatically generated title slide)] --- # Interesting links By far not complete, but check this out: ## Generating SBOMs <https://github.com/kubernetes-sigs/bom> <https://github.com/anchore/syft> <https://docs.docker.com/engine/sbom/> <https://github.com/ckotzbauer/sbom-operator> <https://github.com/microsoft/sbom-tool> .debug[[sbom/collection-sbom-links.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/collection-sbom-links.md)] --- ## Storing SBOMs <https://github.com/dlorenc/sbom-oci> <https://docs.docker.com/build/attestations/sbom/> <https://dependencytrack.org> .debug[[sbom/collection-sbom-links.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/collection-sbom-links.md)] --- ## Analyzing SBOMs <https://dependencytrack.org> <https://trivy.dev> <https://github.com/openclarity/kubeclarity> <https://github.com/CycloneDX/bom-examples> .debug[[sbom/collection-sbom-links.md](https://git.verleun.org/training/containers.git/tree/main/slides/sbom/collection-sbom-links.md)]